Thursday, September 15, 2011
Wednesday, September 14, 2011
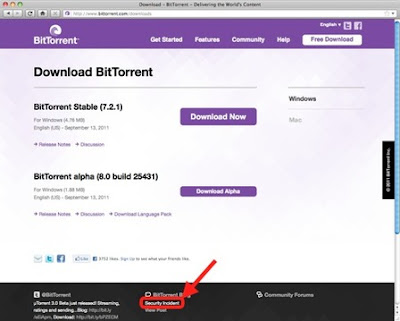
uTorrent & BitTorrent Sites Hacked, Spread Security Shield Malware
Attackers hijacked two popular Torrent websites "bittorrent.com and utorrent.com" and tampered with their download mechanisms, causing visitors trying to obtain file-sharing software to instead receive malware. The site reported on its blog that the attack had occurred at around 04:20 Pacific Daylight Time (11:20 GMT) on Tuesday. Initially, the incursion was also thought to have affected the servers of the main BitTorrent site, but further investigation revealed this site had been unaffected by the attack.
More @ bit.ly/os6I6h
Backtrack 5 Wireless Penetration Testing by Vivek Ramachandran
This book will provide a highly technical and in-depth treatment of Wi-Fi security. The emphasis will be to provide the readers with a deep understanding of the principles behind various attacks and not just a quick how-to guide on publicly available tools.
More @ bit.ly/mQU30L
Friday, September 9, 2011
Fighting the Good Global Cybercrime Fight: Q&A With Security Guru Mikko Hypponen, Part 1
It was once the case that computer viruses and other malicious software were written primarily by hobbyist hackers. Their motivations, for the most part, were simply bragging rights and the respect of their peers -- desirable rewards, to be sure, but certainly not the sole focus of any career. The results of their efforts, meanwhile, could spread only as fast as a floppy disk could travel. How things have changed.
More @ bit.ly/nDDjeb
Fighting the Good Global Cybercrime Fight: Q&A With Security Guru Mikko Hypponen, Part 2
Mikko Hypponen has spent the past 20-plus years studying malicious software, including everything from "Brain" -- the first PC virus, dating back to 1986 -- all the way up to Stuxnet and today's most sophisticated global malware. He's widely considered one of the world's foremost experts on information security, and he's played a key role in taking down numerous international rings of cybercriminals.
More @ bit.ly/o29dhj
Seattle: Solidarity for the win - victory against Chase Bank
Seattle Solidarity Network gets a Chase Bank customer $1000 he was owed by a swift direct action campaign.
Seattle Solidarity Network member Neftali walked out of a Chase Bank in downtown Seattle on Thursday with a check for $1,000 in his hands. This is something that in and of itself is not unusual. He is a Chase customer. Plenty of customers walk out of Chase Bank with money. But this was not just any check. This was a check issued by the bank to correct an error that they had made months ago, and he got that money because Seattle Solidarity (SeaSol for short) helped him fight Chase Bank.
A long-time member of SeaSol, Neftali, was converting $3000 out of his major corporate bank account into Canadian dollars. He presented his valid temporary license along with his expired photo ID during the initial transaction, and it was sufficient and accepted by the teller. When the money was ready and he returned to pick it up, the assistant manger hassled him again and again regarding his form of ID and said that he needed a US passport, seemingly insinuating he did not have legal immigration status. After he complained to the manager, they let him use his card and pin as a form of ID-which is standard procedure at Chase. The teller opened the envelope and gave him $1785, when he was supposed to receive $2785.
He did not realize they shorted him at first and went on his vacation after leaving the bank, flustered about the entire interaction. When he got back to the states he realized that they had shorted him $1000 after looking at his transaction receipt. He confronted the assistant manager, explaining that he thought they probably only forgot the extra 10 $100 bills in the envelope which was mistakenly not given to him-- and wanted them to check the video. She wouldn't believe him and refused to let him watch the video of the teller counting the money. She did, however, admit that the teller broke policy by opening the envelope and not directly handing him it.
Once he realized he was not going to get anywhere by dealing directly with the bank, he brought the issue to the attention of SeaSol. After discussion and research the group decided to take on the fight. On May 31, we delivered a demand delivery with about 30 people to the manager of the Chase branch where the transaction occurred. This demand was very simple - show us the tape of the teller transaction or give our member his money. We gave them two weeks to do one or the other, and if not further action would be taken.
More @ bit.ly/pEhat9
Federal injunction issued as Longshoremen storm Longview port
A federal judge ordered union protesters to stop using illegal tactics Thursday as they battle for the right to work at a new grain terminal in Washington state.
U.S. District Judge Ronald Leighton issued a preliminary injunction to restrict union activity, saying there was no defense for the aggressive tactics used in recent days. Protesters twice blocked the pathway of a train carrying grain to the terminal at the Port of Longview on Wednesday, and early Thursday morning hundreds of them stormed the facility, overwhelmed guards, dumped grain and broke windows, police said.
The dispute halted work at four other Washington ports, including Seattle, on Thursday as hundreds of longshoremen refused to show up or walked off the job.
Leighton said he felt like a paper tiger because the International Longshore and Warehouse Union clearly ignored a temporary restraining order he issued last week with similar limits. He scheduled a hearing for next Thursday to determine whether the union should be held in civil contempt.
"The regard for the law is absent here," the judge said. "Somebody is going to be hurt seriously."
Six guards were trapped for a couple of hours after at least 500 Longshoremen broke down gates about 4:30 a.m. and smashed windows in the guard shack, Longview Police Chief Jim Duscha said. He initially referred to the guards as "hostages," but later retracted that after the guards clarified no one had threatened them.
"The guards absolutely could not get out," Duscha said. "They feared for their lives because of the size of the crowd and the hostility of the crowd."
No one was hurt, and nobody has been arrested - although Duscha said that could change if police are able to use surveillance video or other means to identify the protesters.
Most of the protesters returned to their union hall after cutting train brake lines and spilling grain from a car at the EGT terminal, Duscha said. They also pushed a private security vehicle into a ditch.
The union believes it has the right to work at the facility, but the company has hired a contractor that's staffing a workforce of laborers from another union, the Portland-based Operating Engineers Local 701. Representatives of the engineers union did not immediately return a call seeking comment.
In Seattle, Tacoma, Everett and Anacortes, hundreds of Longshore workers failed to show up or walked off the job Thursday in apparent solidarity with the Longview activists, halting work at those ports. Union leaders said they had not called for any such actions.
"It appears the members have taken action on their own," said ILWU spokesman Craig Merrilees from union headquarters in San Francisco.
He said some workers might have been motivated by a photograph of ILWU President Bob McElrath in police custody in Longview on Wednesday.
McElrath was not arrested, but an Associated Press photo showed him being grabbed by several police officers before union activists intervened and grabbed him back.
Police arrested 19 protesters as they blocked railroad tracks on Wednesday night, allowing the train to finally arrive at the terminal.
More @ bit.ly/oUgdwo
Tuesday, September 6, 2011
Israeli-Turkish Cyberwar Begins
Amid the current diplomatic impasse between Ankara and Jerusalem, Turkish hackers hijacked some 350 Israeli websites on Sunday evening, launching a Domain Name System (DNS) attack on dozens of other websites as well.
Israeli IT analysts said Tuesday the DNS hijacking is likely to be, in fact, a "test-run" ahead of a major attack on Israeli domains.
Visitors to some of the sites were diverted to a page declaring it was “World Hackers Day."
At least seven high-profile websites outside Israel were also hijacked, including those of The Telegraph, Acer, National Geographic, UPS and Vodafone.
Hackers calling themselves the "TurkGuvenligi group" claimed they had done the cyber-attack. TurkGuvenligi translates as "Turkish security."
"The hack represents a 10%-15% spike compared to the average number of daily hacks of Israeli websites," Shai Blitzblau, head of Maglan-Computer Warfare and Network Intelligence Labs, explained.
More @ bit.ly/pXw3I3
Israeli IT analysts said Tuesday the DNS hijacking is likely to be, in fact, a "test-run" ahead of a major attack on Israeli domains.
Visitors to some of the sites were diverted to a page declaring it was “World Hackers Day."
At least seven high-profile websites outside Israel were also hijacked, including those of The Telegraph, Acer, National Geographic, UPS and Vodafone.
Hackers calling themselves the "TurkGuvenligi group" claimed they had done the cyber-attack. TurkGuvenligi translates as "Turkish security."
"The hack represents a 10%-15% spike compared to the average number of daily hacks of Israeli websites," Shai Blitzblau, head of Maglan-Computer Warfare and Network Intelligence Labs, explained.
More @ bit.ly/pXw3I3
Registry Decoder Digital Forensics Software
Digital forensics deals with the analysis of artifacts on all types of digital devices. One of the most prevalent analysis techniques performed is that of the registry hives contained in Microsoft Windows operating systems. Registry Decoder was developed with the purpose of providing a single tool for the acquisition, analysis, and reporting of registry contents. To learn the history of this project, please see the history page.
Registry Decoder is a free and open source tool. The online acquisition component can be accessed at: http://code.google.com/p/regdecoderlive/ and the offline analysis component accessed at: http://code.google.com/p/registrydecoder/.
All functionality contained within the two components is exposed to a graphical user interface, and the tool aims to provide even novice investigators with powerful analysis capabilities.
More @ bit.ly/qcQTP1
Registry Decoder is a free and open source tool. The online acquisition component can be accessed at: http://code.google.com/p/regdecoderlive/ and the offline analysis component accessed at: http://code.google.com/p/registrydecoder/.
All functionality contained within the two components is exposed to a graphical user interface, and the tool aims to provide even novice investigators with powerful analysis capabilities.
More @ bit.ly/qcQTP1
Solidarity action for a comrade detained in Norway
Andre is a Norwegian comrade, our loyal and good friend who had the misfortune to experience psychological repression.whilst fearing for his life and freedom
Andre moved to Tromsø (north of Norway) in August 2010. Since then, he has been almost totally socially isolated.
Andre has a long history of bad treatment and social exclusion. These issues go back to his childhood days where he experienced sexual abuse which was not considered execrable by his surrounding environment.
Andre visited UNN asking for some very mild medical treatment, mostly relaxing therapy, resting and sleep. The reasons: he received some threats from numerous individuals or group of individuals involved with organized crime, which resulted to a psychological collapse. However, the hospital stuff pushed him into forced medication and locked him in the hospital against his will while Andre’s case looks much simpler. It’s been almost three weeks since the Andre started to feel seriously concerned about his life. He constantly experiences that some hospital stuff act inappropriately against him; calling him names or throwing insults. He feels terrorized. He has reason to believe the hospital is involved.
He has tried to sort out the case by speaking to a lawyer but there were no positive results. His lawyer seems to be reluctant to help him while Andre's situation is worsening day by day.
We demand:
1) The hospital stuff to listen what Andre really wants and respect his rights and stop any possible abuse
2) Andre to have access to legal help and advice
3) To complete his treatment based only on what he needs and be released immediately after to the U.K
In solidarity with Andre
PETITION FOR THE RELEASE OF ANDRE DAHL JENSEN
Andre Dahl Jensen, a political activist from Norway is currently being held within a psychiatric ward (UNN Tromso) in Tromso (Norway), on the belief that he suffers delusions, which the doctors have said only to occur when he is in Norway (the idea of regional psychosis being absurd), and on the belief that his political views are caused by mental illness. Many can vouch for his mental stability.
The people in his life know for a FACT that he is indeed a stable man who is currently being held imprisoned for very little reason. Since entering the hospital he has been told on numerous occasions by white supremacists that are being kept there that "They will get him" and other threats. The staff there are also described as malicious and cruel.
Andre himself is trying to leave for the United Kingdom, where he will be housed with friends, while looking for work.
http://www.gopetition.com/petitions/the-release-of-a-political-prisoner-and-activist.html
Here is what you can do to help : (Please contact them as often as possible )
Email the hospital directly as often as you can :
post@unn.no
More @ bit.ly/p74V93
Andre moved to Tromsø (north of Norway) in August 2010. Since then, he has been almost totally socially isolated.
Andre has a long history of bad treatment and social exclusion. These issues go back to his childhood days where he experienced sexual abuse which was not considered execrable by his surrounding environment.
Andre visited UNN asking for some very mild medical treatment, mostly relaxing therapy, resting and sleep. The reasons: he received some threats from numerous individuals or group of individuals involved with organized crime, which resulted to a psychological collapse. However, the hospital stuff pushed him into forced medication and locked him in the hospital against his will while Andre’s case looks much simpler. It’s been almost three weeks since the Andre started to feel seriously concerned about his life. He constantly experiences that some hospital stuff act inappropriately against him; calling him names or throwing insults. He feels terrorized. He has reason to believe the hospital is involved.
He has tried to sort out the case by speaking to a lawyer but there were no positive results. His lawyer seems to be reluctant to help him while Andre's situation is worsening day by day.
We demand:
1) The hospital stuff to listen what Andre really wants and respect his rights and stop any possible abuse
2) Andre to have access to legal help and advice
3) To complete his treatment based only on what he needs and be released immediately after to the U.K
In solidarity with Andre
PETITION FOR THE RELEASE OF ANDRE DAHL JENSEN
Andre Dahl Jensen, a political activist from Norway is currently being held within a psychiatric ward (UNN Tromso) in Tromso (Norway), on the belief that he suffers delusions, which the doctors have said only to occur when he is in Norway (the idea of regional psychosis being absurd), and on the belief that his political views are caused by mental illness. Many can vouch for his mental stability.
The people in his life know for a FACT that he is indeed a stable man who is currently being held imprisoned for very little reason. Since entering the hospital he has been told on numerous occasions by white supremacists that are being kept there that "They will get him" and other threats. The staff there are also described as malicious and cruel.
Andre himself is trying to leave for the United Kingdom, where he will be housed with friends, while looking for work.
http://www.gopetition.com/petitions/the-release-of-a-political-prisoner-and-activist.html
Here is what you can do to help : (Please contact them as often as possible )
Email the hospital directly as often as you can :
post@unn.no
More @ bit.ly/p74V93
Copwatch Conference: Seeking alternatives to the police
Despite only occasionally surfacing in the news -- with more than 1,000 G20 arrests, tasering deaths, lethal shootings and abuse in holding cells -- police misconduct is not only widespread and historic it is also deeply entrenched, said presenters at a major conference on policing last week in Winnipeg.
The International Copwatching Conference was hosted by Winnipeg Copwatch, an anti police-brutality group founded in 2007. The July 22-24 event attracted participants from every major Canadian city, as well as the U.S.
It's been just over a year since the gates of "Torontonamo Bay", the nickname for the makeshift prison which caged 1,105 demonstrators during last June's G20 mass protests in Toronto, finally closed. During that weekend, the largest police deployment in Canada's history of 20,000 officers led to gunpoint raids, dozens of activists facing years of legal battles, and emerging stories of threats, homophobia, and sexual harassment.
In the wake of these and other widely publicised incidents of police misconduct in Canada -- including the deaths of Dudley George, Robert Dziekanski, J.J. Harper, Matthew Dumas, and the failure to investigate more than 600 missing and murdered Indigenous women -- concern with police brutality in Canada brought several hundred people to Winnipeg.
"These incidents are not isolated -- they are integral to policing," said keynote speaker Andrea Ritchie, a lawyer and co-founder of the group INCITE! Women of Color Against Violence. "Until we produce a world that does not contain or produce police and prisons, we will never live in a world without violence or imagine alternatives."
At the conference, it was not only police departments who faced criticism. Workshops and panels addressed problems of immigration and border officers, prison guards, as well as the capitalist economic system. Immigrants and refugees face racial profiling, detention, deportation, only set to increase with the Conservatives' proposed immigration laws.
"Copwatching" is a tactic which started in the Black Panther movement but was later taken up by organizers in Berkeley, California, following several high-profile killings and beatings of men of colour by police in the early 1990s, including Rodney King's videotaped assault in Los Angeles, which led to extensive rioting, protests and demands for accountability.
The aim of copwatching, organizers said, is to document and deter police misconduct by observing police and holding them publically accountable.
"The goal of copwatching is to show police we are watching them too, to show people that resistance is possible, and to denounce what is happening on the streets," said François Du Canal, with Montreal's Collective Opposed to Police Brutality.
The international conference was the second gathering of the growing copwatching movement, following one hosted by the founding Berkeley Copwatch in 2007. Copwatch groups -- as well as others who use similar strategies -- use tactics including videotaping police, filing official complaints, protesting police misconduct, and hosting "know your rights" public workshops and sharing circles.
"Proactively our tactic is to educate about rights, to observe the police, to build relationships in the community," said Andrea Pritchett, with Berkeley Copwatch.
More @ bit.ly/nPMX25
The International Copwatching Conference was hosted by Winnipeg Copwatch, an anti police-brutality group founded in 2007. The July 22-24 event attracted participants from every major Canadian city, as well as the U.S.
It's been just over a year since the gates of "Torontonamo Bay", the nickname for the makeshift prison which caged 1,105 demonstrators during last June's G20 mass protests in Toronto, finally closed. During that weekend, the largest police deployment in Canada's history of 20,000 officers led to gunpoint raids, dozens of activists facing years of legal battles, and emerging stories of threats, homophobia, and sexual harassment.
In the wake of these and other widely publicised incidents of police misconduct in Canada -- including the deaths of Dudley George, Robert Dziekanski, J.J. Harper, Matthew Dumas, and the failure to investigate more than 600 missing and murdered Indigenous women -- concern with police brutality in Canada brought several hundred people to Winnipeg.
"These incidents are not isolated -- they are integral to policing," said keynote speaker Andrea Ritchie, a lawyer and co-founder of the group INCITE! Women of Color Against Violence. "Until we produce a world that does not contain or produce police and prisons, we will never live in a world without violence or imagine alternatives."
At the conference, it was not only police departments who faced criticism. Workshops and panels addressed problems of immigration and border officers, prison guards, as well as the capitalist economic system. Immigrants and refugees face racial profiling, detention, deportation, only set to increase with the Conservatives' proposed immigration laws.
"Copwatching" is a tactic which started in the Black Panther movement but was later taken up by organizers in Berkeley, California, following several high-profile killings and beatings of men of colour by police in the early 1990s, including Rodney King's videotaped assault in Los Angeles, which led to extensive rioting, protests and demands for accountability.
The aim of copwatching, organizers said, is to document and deter police misconduct by observing police and holding them publically accountable.
"The goal of copwatching is to show police we are watching them too, to show people that resistance is possible, and to denounce what is happening on the streets," said François Du Canal, with Montreal's Collective Opposed to Police Brutality.
The international conference was the second gathering of the growing copwatching movement, following one hosted by the founding Berkeley Copwatch in 2007. Copwatch groups -- as well as others who use similar strategies -- use tactics including videotaping police, filing official complaints, protesting police misconduct, and hosting "know your rights" public workshops and sharing circles.
"Proactively our tactic is to educate about rights, to observe the police, to build relationships in the community," said Andrea Pritchett, with Berkeley Copwatch.
More @ bit.ly/nPMX25
Department of Homeland Security warns Anonymous Hackers
The US Department of Homeland Security issued a warning to the security community regarding the planned activities of Anonymous.The DHS National Cybersecurity and Communications Integration Center (NCCIC), warns financial services companies about Anonymous’ attempts to “solicit ideologically dissatisfied, sympathetic employees.”
The bulletin warned:
Anonymous have tweeted about a tool, they call #RefRef which is believed to cause huge damage. However its damage potential remains unknown.
“Anonymous has stated publicly that the tool will be ready for wider use by the group in September 2011,” the DHS said. “But though there have been several publicly available tools that claim to be versions of #RefRef, so far it’s unclear “what the true capabilities of #RefRef are.”
They have also mentioned Apache Killer tool that can be used to launch denial of service attacks.
The DHS alert also warns of three cyber attacks:
More @ bit.ly/oOV08T
The bulletin warned:
“unwilling coercion through embarrassment or blackmail may be a risk to personnel,”They have alsowarned about the new tools that Anonymous has said it plans to use in launching future attacks.
Anonymous have tweeted about a tool, they call #RefRef which is believed to cause huge damage. However its damage potential remains unknown.
“Anonymous has stated publicly that the tool will be ready for wider use by the group in September 2011,” the DHS said. “But though there have been several publicly available tools that claim to be versions of #RefRef, so far it’s unclear “what the true capabilities of #RefRef are.”
They have also mentioned Apache Killer tool that can be used to launch denial of service attacks.
The DHS alert also warns of three cyber attacks:
- Occupy Wall Street
- Operation Facebook
- Project Mayhem
Operation Facebook is to take place on November 11, targeting the facebook for its alleged privacy violations.
Project Mayhem is scheduled for Dec 21, 2012. Not much details are available about this plan.More @ bit.ly/oOV08T
Nurses Protest in 60 Cities, Demanding Tax on Wall Street
Thousands of nurses and supporters descended on their local Congressional offices nationwide Thursday, demanding that Wall Street pay for the crisis it created.
The 60 protests in 21 states targeted both Democrats and Republicans, with austerity champions like Eric Cantor of Virginia and Michelle Bachmann of Minnesota singled out for special attention. A blockade outside Cantor’s office forced his staffers to meet with a delegation, a request they had repeatedly refused.
Soup kitchens outside Congressional offices highlighted the devastation wrought by the economy’s collapse and worsened when politicians rip into social programs. Hundreds lined up outside Democratic leader Nancy Pelosi’s San Francisco office to receive a meal.
Katie Oppenheim of the Michigan Nurses Association joined a group that served a meal in Jackson. When the nurses attempted to talk with Republican Tim Walberg, the receptionist would speak with them only from behind her bulletproof glass.
“This is one more fight among many in the country to convince corporate America we will not back down,” said Oppenheim, who chairs the professional nurse council at the University of Michigan health system.
More @ bit.ly/quJPou
The 60 protests in 21 states targeted both Democrats and Republicans, with austerity champions like Eric Cantor of Virginia and Michelle Bachmann of Minnesota singled out for special attention. A blockade outside Cantor’s office forced his staffers to meet with a delegation, a request they had repeatedly refused.
Soup kitchens outside Congressional offices highlighted the devastation wrought by the economy’s collapse and worsened when politicians rip into social programs. Hundreds lined up outside Democratic leader Nancy Pelosi’s San Francisco office to receive a meal.
Katie Oppenheim of the Michigan Nurses Association joined a group that served a meal in Jackson. When the nurses attempted to talk with Republican Tim Walberg, the receptionist would speak with them only from behind her bulletproof glass.
“This is one more fight among many in the country to convince corporate America we will not back down,” said Oppenheim, who chairs the professional nurse council at the University of Michigan health system.
More @ bit.ly/quJPou
Antisec Messes with Texas, Attacks Dozens of Police Systems and Chief Emails
| Greetings professional hypocrites in law enforcement! Having a slow day behind the desk, filing papers, staring at your colleague's fine posterior? What have you been up to since our last visit? Don't answer that. We already know. Lewd jokes? Check. Racist chain mails? Check. You lost your radio license? Lulz. Playing on the fears of voters? Check. But we already figured that. Our friends, allies, and vessels are threatened with 10+ years in prison. Yet terrorists like Luis Posada Carilles go free. This hypocritical and paranoid reaction puts us and the citizens you are supposed to protect in the same boat. You call us a national security risk. Yet BATFE guns go directly to drug dealers so they can take out rivals who don't launder money through backrooms of dominant banks. Any press can check court documents from operations like 'Fast and Furious'. Who came up with that one? What you didn't see 'From Dusk 'til Dawn'? Better title. Be more creative next time. In retaliation for the arrests of dozens of alleged Anonymous suspects, we opened fire on dozens of Texas police departments and stole boatloads of classified police documents and police chief emails across the state. During the San Jose courtdate we defaced and gave out live backdoor and admin access to the website TexasPoliceChiefs.org while allied ships launched ddos attacks upon Justice.gov and other law enforcement websites. For every defendant in the anonymous "conspiracy" we are attacking two top Texas police chiefs, leaking 3GB of their private emails and attachments. Mind you, we don't expect a sane response. Even a few insults would have been better than the way you cowards hide behind protocol, innuendo, and your badge. For more than a month we have been lurking their emails, law enforcement portals, and records and reporting systems. We leaked a few teasers including access to fbivirtualacademy.edu, several classified documents, voicemail recordings, live passwords, and even some dirty pictures. To continue the fighting spirit of WikiLeaks, we want to share the full Texas collection and expose these bumbling fools and all their secrets to the world. Thousands of documents are available on tor hidden services / bittorrent and include several dozen FBI, Border Patrol, and counter-terrorism documents classified as "law enforcement sensitive" and "for official use only". The emails also included police records, internal affairs investigations, meeting notes, training materials, officer rosters, security audits, and live password information to government systems. The private chief emails also included several racist and sexist chain email forwards and personal details sure to embarrass, discredit, and incriminate several of these so-called "community leaders". We are attacking Texas law enforcement as part of "Chinga La Migra" as they continue to harass immigrants and use border patrol operations as a cover for their backwards racist prejudice. The notoriously racist police state of Texas recently passed SB 9 and "Secure Comminities" anti-immigration laws. Texas is well known and hated for being full of Minutemen, Tea Party and KKK groups, murdering the most amount of innocent people on death row, and giving us the Bush and Cheney administration. Two months ago on the 1st we attacked the Arizona DPS and defaced several Fraternal Order of Police websites. One month ago we "Shot The Sheriff" and released 10GB of private law enforcement data while defacing dozens of police department websites in several states in the south. A week ago we released private emails belonging to Richard T. Garcia, VP of Texas-based Vanguard Defense Industries, and also a former FBI agent and current Infragard executive board member. More @ bit.ly/r6zHau |
Tuesday, August 30, 2011
An update on attempted man-in-the-middle attacks
Today we received reports of attempted SSL man-in-the-middle (MITM) attacks against Google users, whereby someone tried to get between them and encrypted Google services. The people affected were primarily located in Iran. The attacker used a fraudulent SSL certificate issued by DigiNotar, a root certificate authority that should not issue certificates for Google (and has since revoked it).
Google Chrome users were protected from this attack because Chrome was able to detect the fraudulent certificate.
More @ bit.ly/qzemez
Microsoft UI has officially entered the realm of self-parody
This is genuinely Microsoft’s idea of a “streamlined”, “optimized” UI for Windows Explorer. They were so proud of it they wrote a blog post about it.
The post is a sort of masterpiece of crazy rationalization, but I think my favourite part may be this screenshot:
Here, they proudly overlay the UI with data from their research into how often various commands are used. They use this to show that “the commands that make up 84% of what users do in Explorer are now in one tab”. But the more important thing is that the remaining 50% of the bar is taken up by buttons that nobody will ever use, ever, even according to Microsoft’s own research. And yet somehow they remain smack bang in the middle of the interface. The insanity is further enriched by this graph:
More @ bit.ly/qM4MRS
Monday, August 29, 2011
Sunday, August 28, 2011
So you want to be a video game programmer?
This post is a sequel of sorts to my How do I get a job designing video games. The good new is — if you’re a programmer — that nearly all video game companies are hiring programmers at all times. Demand is never satisfied. And the salaries are very very competitive.
The bad news is that it takes a hell of a lot of work to both be and become a great game programmer. Or maybe that isn’t such bad news, because you absolutely love programming, computers, and video games, right? If not, stop and do not goto 20.
I’m going to break this post down into a number of sub-posts, so this first one is going to be on what kinds of programming video game teams need. I’ll have followup posts on things like “how to get started” and “the interview.”
There are a couple of broad categories of programmers working on video game teams. If programmer is your player class, then the following types are your spec. Programmers are all warlocks and mages so instead of “demonology” or “frost” you can choose from below. (NOTE: if you don’t get this joke, you don’t play enough video games) This is the real world however, and many programmers dual (or even triple) spec — i.e. they handle multiple specialties.
More @ bit.ly/rbGzAM
The bad news is that it takes a hell of a lot of work to both be and become a great game programmer. Or maybe that isn’t such bad news, because you absolutely love programming, computers, and video games, right? If not, stop and do not goto 20.
I’m going to break this post down into a number of sub-posts, so this first one is going to be on what kinds of programming video game teams need. I’ll have followup posts on things like “how to get started” and “the interview.”
There are a couple of broad categories of programmers working on video game teams. If programmer is your player class, then the following types are your spec. Programmers are all warlocks and mages so instead of “demonology” or “frost” you can choose from below. (NOTE: if you don’t get this joke, you don’t play enough video games) This is the real world however, and many programmers dual (or even triple) spec — i.e. they handle multiple specialties.
More @ bit.ly/rbGzAM
Antivirus Software Pioneer Gets Dose of Reality
John McAfee knows about risk. A mathematician by training, in the late 1980s he developed the antivirus computer software program that has become a household name. In the 1990s he pioneered instant-messaging. In both cases, he grew bored and cashed out. At his peak, he was reportedly worth about $100 million.
"I don't know and that's the honest truth, eventually you have so many resources that a tiny fluctuation in the market can make you worth ten million dollars more in the morning and ten million dollars less in the evening," he explained of his ever-changing net worth.
Like many wealthy Americans, McAfee was hit hard with the simultaneous collapse of real estate, stocks and Wall Street investment banks. But he got whacked more than most, since much of his fortune was tied up in luxury properties.
"Oddly enough, when real estate markets crash, it's the higher end properties that crash the most ... simply because they're not necessities," he said. "My father always said, 'Real estate, you can't lose in real estate' ... you know, oddly enough you can."
Last Saturday, auctioneers worked up bids for his 80-acre retreat in the high desert of Rodeo, N.M. With a private airstrip and hangar, it's a slice of paradise, and it's all up for grabs.
"Everything that you see, from the real estate, the house, the automobiles, artwork, furniture, the entire ball of wax," McAfee told ABC News.
Raising the stakes for McAfee, it's an absolute auction: The highest bid wins, no matter how low it is. "It means if only one person shows up and they bid fifty cents, that's the amount of money I get," he said.
McAfee's net worth dropped from within the ballpark of $100 million to less than $10 million, he told ABC News. But instead of feeling a sense of loss, he says he feels free.
"I feel a sense of freedom," he said. "People think that it's a joy to own things. But it really isn't."
McAfee has sold his private twin-engine plane, beachfront property in Hawaii and a Colorado mansion in the shadow of Pike's Peak. His posh New Mexico getaway is the last property to hit the auction block.
"At one point, I had five houses in five different locations and it's impractical, it's almost insane to have that much real estate," he conceded. "You can only be in one place at a time."
"We are the ultimate consumer society," he said. "If you succeed within that culture, then you're simply more bonded to it. You feel like, 'Yes, I've got all this money, the ability to get things' ... and so you just do it. People buy yachts, they buy jets, they buy multiple homes."
McAfee himself indulged his whims and passions, spending millions to promote the sport of aero-trekking: tiny motorized kites that enthusiasts fly to explore the remotest corners of the country.
He built an aero-trekking playground in the Rodeo desert, which was auctioned off for $405,000 -- along with the vintage airstream trailers where his aero-trekking friends, known as "the sky gypsies," would stay, as well as his own customized camper, once owned by Howard Hughes.
More @ abcn.ws/qFgB7Q
"I don't know and that's the honest truth, eventually you have so many resources that a tiny fluctuation in the market can make you worth ten million dollars more in the morning and ten million dollars less in the evening," he explained of his ever-changing net worth.
Like many wealthy Americans, McAfee was hit hard with the simultaneous collapse of real estate, stocks and Wall Street investment banks. But he got whacked more than most, since much of his fortune was tied up in luxury properties.
"Oddly enough, when real estate markets crash, it's the higher end properties that crash the most ... simply because they're not necessities," he said. "My father always said, 'Real estate, you can't lose in real estate' ... you know, oddly enough you can."
Last Saturday, auctioneers worked up bids for his 80-acre retreat in the high desert of Rodeo, N.M. With a private airstrip and hangar, it's a slice of paradise, and it's all up for grabs.
"Everything that you see, from the real estate, the house, the automobiles, artwork, furniture, the entire ball of wax," McAfee told ABC News.
Raising the stakes for McAfee, it's an absolute auction: The highest bid wins, no matter how low it is. "It means if only one person shows up and they bid fifty cents, that's the amount of money I get," he said.
McAfee's net worth dropped from within the ballpark of $100 million to less than $10 million, he told ABC News. But instead of feeling a sense of loss, he says he feels free.
"I feel a sense of freedom," he said. "People think that it's a joy to own things. But it really isn't."
McAfee has sold his private twin-engine plane, beachfront property in Hawaii and a Colorado mansion in the shadow of Pike's Peak. His posh New Mexico getaway is the last property to hit the auction block.
"At one point, I had five houses in five different locations and it's impractical, it's almost insane to have that much real estate," he conceded. "You can only be in one place at a time."
McAfee: 'We Are the Ultimate Consumer Society'
McAfee admits that he got caught up in the culture of consumption."We are the ultimate consumer society," he said. "If you succeed within that culture, then you're simply more bonded to it. You feel like, 'Yes, I've got all this money, the ability to get things' ... and so you just do it. People buy yachts, they buy jets, they buy multiple homes."
McAfee himself indulged his whims and passions, spending millions to promote the sport of aero-trekking: tiny motorized kites that enthusiasts fly to explore the remotest corners of the country.
He built an aero-trekking playground in the Rodeo desert, which was auctioned off for $405,000 -- along with the vintage airstream trailers where his aero-trekking friends, known as "the sky gypsies," would stay, as well as his own customized camper, once owned by Howard Hughes.
More @ abcn.ws/qFgB7Q
Saturday, August 27, 2011
Simple Security for Wireless
In early August, at the Def Con conference -- a major annual gathering of computer hackers -- someone apparently hacked into many of the attendees' cell phones, in what may have been the first successful breach of a 4G cellular network. If early reports are correct, the incident was a man-in-the-middle (MITM) attack, so called because the attacker interposes himself between two other wireless devices.
Coincidentally, a week later, at the 20th Usenix Security Symposium, MIT researchers presented the first security scheme that can automatically create connections between wireless devices and still defend against MITM attacks. Previously, thwarting the attacks required password protection or some additional communication mechanism, such as an infrared transmitter.
Showcasing novel ways to breach security is something of a tradition at Def Con. In previous years, MITM attacks had been launched against attendees' Wi-Fi devices; indeed, the MIT researchers demonstrated the effectiveness of their new scheme on a Wi-Fi network. But in principle, MITM attacks can target any type of wireless connection, not only between devices (phones or laptops) and base stations (cell towers or Wi-Fi routers), but also between a phone and a wireless headset, a medical implant and a wrist-mounted monitor, or a computer and a wireless speaker system.
Key change
Ordinarily, when two wireless devices establish a secure connection, they swap cryptographic keys -- the unique codes they use to encrypt their transmissions. In an MITM attack, the attacker tries to broadcast his own key at the exact moment that the key swap takes place. If he's successful, one or both of the devices will mistake him for the other, and he will be able to intercept their transmissions.
Password protection can thwart MITM attacks, assuming the attacker doesn't know the password. But that's not always a safe assumption. At a hotel or airport that offers Wi-Fi, for instance, all authorized users are generally given the same password, which means that any one of them could launch an MITM attack against the others. Moreover, many casual computer users find it so complicated to set up home Wi-Fi networks that they don't bother to protect them; when they do, they often select passwords that are too simple to provide much security. That's led to the marketing of Wi-Fi transmitters with push-button configuration: To establish a secure link, you simply push a button on top of the transmitter and a corresponding button (or virtual button) on your wireless device. But such systems remain vulnerable to MITM attacks.
"None of these solutions are quite satisfactory," says Nickolai Zeldovich, the Douglas Ross (1954) Career Development Assistant Professor of Software Technology, who developed the new security scheme together with Dina Katabi, the Class of 1947 Career Development Associate Professor of Computer Science and Engineering, as well as postdoc Nabeel Ahmed and graduate student Shyam Gollakota, all of MIT's Department of Electrical Engineering and Computer Science. "The cool thing about this work is that it takes some insight from somewhat of a different field, from wireless communication -- actually, fairly low-level details about what can happen in terms of wireless signals -- and observes that, hey, if you assume some of these properties about wireless networks, you can actually get stronger guarantees."
More @ bit.ly/qfshwd
Coincidentally, a week later, at the 20th Usenix Security Symposium, MIT researchers presented the first security scheme that can automatically create connections between wireless devices and still defend against MITM attacks. Previously, thwarting the attacks required password protection or some additional communication mechanism, such as an infrared transmitter.
Showcasing novel ways to breach security is something of a tradition at Def Con. In previous years, MITM attacks had been launched against attendees' Wi-Fi devices; indeed, the MIT researchers demonstrated the effectiveness of their new scheme on a Wi-Fi network. But in principle, MITM attacks can target any type of wireless connection, not only between devices (phones or laptops) and base stations (cell towers or Wi-Fi routers), but also between a phone and a wireless headset, a medical implant and a wrist-mounted monitor, or a computer and a wireless speaker system.
Key change
Ordinarily, when two wireless devices establish a secure connection, they swap cryptographic keys -- the unique codes they use to encrypt their transmissions. In an MITM attack, the attacker tries to broadcast his own key at the exact moment that the key swap takes place. If he's successful, one or both of the devices will mistake him for the other, and he will be able to intercept their transmissions.
Password protection can thwart MITM attacks, assuming the attacker doesn't know the password. But that's not always a safe assumption. At a hotel or airport that offers Wi-Fi, for instance, all authorized users are generally given the same password, which means that any one of them could launch an MITM attack against the others. Moreover, many casual computer users find it so complicated to set up home Wi-Fi networks that they don't bother to protect them; when they do, they often select passwords that are too simple to provide much security. That's led to the marketing of Wi-Fi transmitters with push-button configuration: To establish a secure link, you simply push a button on top of the transmitter and a corresponding button (or virtual button) on your wireless device. But such systems remain vulnerable to MITM attacks.
"None of these solutions are quite satisfactory," says Nickolai Zeldovich, the Douglas Ross (1954) Career Development Assistant Professor of Software Technology, who developed the new security scheme together with Dina Katabi, the Class of 1947 Career Development Associate Professor of Computer Science and Engineering, as well as postdoc Nabeel Ahmed and graduate student Shyam Gollakota, all of MIT's Department of Electrical Engineering and Computer Science. "The cool thing about this work is that it takes some insight from somewhat of a different field, from wireless communication -- actually, fairly low-level details about what can happen in terms of wireless signals -- and observes that, hey, if you assume some of these properties about wireless networks, you can actually get stronger guarantees."
More @ bit.ly/qfshwd
Friday, August 26, 2011
Sunday, August 21, 2011
Linux Journal goes 100% digital
What is the last print issue I should expect to see?The last issue printed was the August 2011 issue.
I have a U.S. print subscription. What happens?As long as we have your email address, you don’t need to do anything. If you are concerned that we do not have your email address, or if you prefer to receive notifications at another email address, please visit linuxjournal.com/updateaccount. On the 1st of every month, you will receive a notification via email to download the latest issue of Linux Journal.
I have an international print subscription. What happens?As long as we have your email address, you don’t need to do anything. If you are concerned that we do not have your email address, or if you prefer to receive notifications at another email address, please visit linuxjournal.com/updateaccount. Your current subscription term will be extended based on the remaining value of your subscription. For example, if your current remaining subscription value is $52.13 USD (say you paid $69.50 and received 3 copies), the term will be extended by 21 issues based on the issue value of $2.46.
I have a print + digital (“combo”) subscription. What happens?You don’t need to do anything; we already have your email address. Your current subscription term will be extended based on the remaining value of your subscription. For example, if your current remaining subscription value is $29.63 USD (say you paid $39.50 and received 3 copies), the term will be extended by 12 issues based on the issue value of $2.46.
I already have a digital-only subscription. Does this announcement affect me?
You don’t need to do anything, and you will continue to receive your digital subscription. However, if you would like to upgrade to the new, enhanced online digital edition from Texterity, simply visit linuxjournal.com/updateaccount. There is no additional charge for upgrading.
When will I see my first digital issue?Current subscribers can expect to see the September 2011 issue of Linux Journal in their e-mail inboxes on Friday, August 19, 2011. If for any reason you do not receive your copy by the end of that day, please e-mail gm@linuxjournal.com with your full name and postal code.
More @ bit.ly/pGjO48
I have a U.S. print subscription. What happens?As long as we have your email address, you don’t need to do anything. If you are concerned that we do not have your email address, or if you prefer to receive notifications at another email address, please visit linuxjournal.com/updateaccount. On the 1st of every month, you will receive a notification via email to download the latest issue of Linux Journal.
I have an international print subscription. What happens?As long as we have your email address, you don’t need to do anything. If you are concerned that we do not have your email address, or if you prefer to receive notifications at another email address, please visit linuxjournal.com/updateaccount. Your current subscription term will be extended based on the remaining value of your subscription. For example, if your current remaining subscription value is $52.13 USD (say you paid $69.50 and received 3 copies), the term will be extended by 21 issues based on the issue value of $2.46.
I have a print + digital (“combo”) subscription. What happens?You don’t need to do anything; we already have your email address. Your current subscription term will be extended based on the remaining value of your subscription. For example, if your current remaining subscription value is $29.63 USD (say you paid $39.50 and received 3 copies), the term will be extended by 12 issues based on the issue value of $2.46.
I already have a digital-only subscription. Does this announcement affect me?
You don’t need to do anything, and you will continue to receive your digital subscription. However, if you would like to upgrade to the new, enhanced online digital edition from Texterity, simply visit linuxjournal.com/updateaccount. There is no additional charge for upgrading.
When will I see my first digital issue?Current subscribers can expect to see the September 2011 issue of Linux Journal in their e-mail inboxes on Friday, August 19, 2011. If for any reason you do not receive your copy by the end of that day, please e-mail gm@linuxjournal.com with your full name and postal code.
More @ bit.ly/pGjO48
How Google+ Is Like Twitter—but Not in a Good Way
Tech blogger Robert Scoble, the king of the early-adopter crowd, has posted some thoughts about what he likes and doesn’t like about using Google+, and some of his points hit home with me as well. And the more I thought about the new social network and the things it doesn’t do very well, the more similar it seemed to the issues that have also been dogging Twitter for some time. Like Twitter, the Web giant has to figure out how to solve some pretty challenging problems—including the "noisy stream" issue, the problems of search and discovery, and, of course, how to keep people from going away and never coming back.
As more than one person (including Scoble himself) has noted, he isn’t exactly the average user of social tools. As someone with hundreds of thousands of followers, who jumps on every new Web or social tool that comes along—in some cases dominating those new services to the point where they become almost unusable, as some found with FriendFeed—Scoble is definitely an "edge case." But at the same time, that makes him a little like the canary in a coal mine: He can highlight problems that may only become obvious for others much later.
More @ buswk.co/rnIEuC
As more than one person (including Scoble himself) has noted, he isn’t exactly the average user of social tools. As someone with hundreds of thousands of followers, who jumps on every new Web or social tool that comes along—in some cases dominating those new services to the point where they become almost unusable, as some found with FriendFeed—Scoble is definitely an "edge case." But at the same time, that makes him a little like the canary in a coal mine: He can highlight problems that may only become obvious for others much later.
More @ buswk.co/rnIEuC
Thursday, August 18, 2011
Company Scans Your Books For a Dollar – Ship ‘Em In, Get a PDF via Email
Someday my grandchildren will ask me what a printed book looks like. Hell, at the rate we’re going, my children will probably ask the same question. The physical to digital conversion of books just got a lot cheaper with the launch of 1DollarScan.com, based in San Jose, California. An offshoot of the immensely successful BookScan in Japan, 1DollarScan does exactly what its name implies: it scans your documents for a dollar. 100 pages of a book, 10 pages of a business document, 10 business card, etc – you just mail the text in and 1DollarScan will email you back a PDF. While the transition away from print media has been proceeding a pace for a while now, a cheap book scanning service in the US means that thousands of personal libraries will be converted to ones and zeroes, pushing us ever closer to a world where all printed books (Gutenberg to Gladwell) belong in a museum.
Yusuke Ohki started BookScan after he laboriously converted his personal library of 2000+ volumes into digital documents. Now the company has 200+ employees who do nothing but that, and reportedly the service is so popular in Japan there’s an extensive waiting list. 1DollarScan promises to bring the same dependable, quick, and hopefully popular service to the US with its freshly debuted Silicon Valley headquarters. The following video was made for BookScan, not 1DollarScan, so it’s only available in Japanese, but you can see the basic components of the technology in action. Send, slice, scan, and email. From book to PDF in about two weeks. We’ve seen better machines, but 1DollarScan makes scanning books simple, and simple sells.
More @ bit.ly/ph0xn2
Candle flames contain millions of tiny diamonds
(PhysOrg.com) -- The flickering flame of a candle has generated comparisons with the twinkling sparkle of diamonds for centuries, but new research has discovered the likeness owes more to science than the dreams of poets.
Professor Wuzong Zhou, Professor of Chemistry at the University of St Andrews has discovered tiny diamond particles exist in candle flames.
His research has made a scientific leap towards solving a mystery which has befuddled people for thousands of years.
Since the first candle was invented in ancient China more than 2,000 years ago, many have longed to know what hidden secrets its flames contained.
Dr Zhou’s investigation revealed around 1.5 million diamond nanoparticles are created every second in a candle flame as it burns.
The leading academic revealed he uncovered the secret ingredient after a challenge from a fellow scientist in combustion.
Dr Zhou said: “A colleague at another university said to me: “Of course no-one knows what a candle flame is actually made of.
“I told him I believed science could explain everything eventually, so I decided to find out.”
Using a new sampling technique, assisted by his student Mr Zixue Su, he invented himself, he was able to remove particles from the centre of the flame – something never successfully achieved before – and found to his surprise that a candle flame contains all four known forms of carbon.
Dr Zhou said: "This was a surprise because each form is usually created under different conditions."
At the bottom of the flame, it was already known that hydro-carbon molecules existed which were converted into carbon dioxide by the top of the flame.
But the process in between remained a mystery.
Now both diamond nanoparticles and fullerenic particles have been discovered in the centre of the flame, along with graphitic and amorphous carbon.
The discovery could lead to future research into how diamonds, a key substance in industry, could be created more cheaply, and in a more environmentally friendly way.
Dr Zhou added: “Unfortunately the diamond particles are burned away in the process, and converted into carbon dioxide, but this will change the way we view a candle flame forever.”
The famous scientist Michael Faraday in his celebrated 19th century lectures on “The Chemical History of a Candle” said in an 1860 address to the light: “You have the glittering beauty of gold and silver, and the still higher lustre of jewels, like the ruby and diamond; but none of these rival the brilliancy and beauty of flame. What diamond can shine like flame?”
Rosey Barnet, Artistic Director of one of Scotland’s biggest candle manufacturers, Shearer Candles, described the finding as "exciting".
She said: "We were thrilled to hear about the discovery that diamond particles exist in a candle flame.
More @ bit.ly/rheXW7
First Flaws in the Advanced Encryption Standard Used for Internet Banking Identified
Researchers have found a weakness in the AES algorithm. They managed to come up with a clever new attack that can recover the secret key four times easier than anticipated by experts.
The attack is a result of a long-term cryptanalysis project carried out by Andrey Bogdanov (K.U.Leuven, visiting Microsoft Research at the time of obtaining the results), Dmitry Khovratovich (Microsoft Research), and Christian Rechberger (ENS Paris, visiting Microsoft Research).
The AES algorithm is used by hundreds of millions of users worldwide to protect internet banking, wireless communications, and the data on their hard disks. In 2000, the Rijndael algorithm, designed by the Belgian cryptographers Dr. Joan Daemen (STMicroelectronics) and Prof. Vincent Rijmen (K.U.Leuven), was selected as the winner of an open competition organized by the US NIST (National Institute for Standards and Technology). Today AES is used in more than 1700 NIST-validated products and thousands of others; it has been standardized by NIST, ISO, and IEEE and it has been approved by the U.S. National Security Agency (NSA) for protecting secret and even top secret information.
More @ bit.ly/oXBHHB
The attack is a result of a long-term cryptanalysis project carried out by Andrey Bogdanov (K.U.Leuven, visiting Microsoft Research at the time of obtaining the results), Dmitry Khovratovich (Microsoft Research), and Christian Rechberger (ENS Paris, visiting Microsoft Research).
The AES algorithm is used by hundreds of millions of users worldwide to protect internet banking, wireless communications, and the data on their hard disks. In 2000, the Rijndael algorithm, designed by the Belgian cryptographers Dr. Joan Daemen (STMicroelectronics) and Prof. Vincent Rijmen (K.U.Leuven), was selected as the winner of an open competition organized by the US NIST (National Institute for Standards and Technology). Today AES is used in more than 1700 NIST-validated products and thousands of others; it has been standardized by NIST, ISO, and IEEE and it has been approved by the U.S. National Security Agency (NSA) for protecting secret and even top secret information.
More @ bit.ly/oXBHHB
New Anti-Censorship Scheme Could Make It Impossible to Block Individual Web Sites
A radical new approach to thwarting Internet censorship would essentially turn the whole web into a proxy server, making it virtually impossible for a censoring government to block individual sites.
The system is called Telex, and it is the brainchild of computer science researchers at the University of Michigan and the University of Waterloo in Canada. They will present it Aug. 12 at the USENIX Security Symposium in San Francisco.
"This has the potential to shift the arms race regarding censorship to be in favor of free and open communication," said J. Alex Halderman, assistant professor of computer science and engineering at U-M and one of Telex's developers.
"The Internet has the ability to catalyze change by empowering people through information and communication services. Repressive governments have responded by aggressively filtering it. If we can find ways to keep those channels open, we can give more people the ability to take part in free speech and access to information."
Today's typical anticensorship schemes get users around site blocks by routing them through an outside server called a proxy. But the censor can monitor the content of traffic on the whole network, and eventually finds and blocks the proxy, too.
"It creates a kind of cat and mouse game," said Halderman, who was at the blackboard explaining this to his computer and network security class when it hit him that there might be a different approach -- a bigger way to think about the problem.
Here's how Telex would work:
Users install Telex software. Halderman envisions they could download it from an intermittently available website or borrow a copy from a friend.
Internet Service Providers (ISPs) outside the censoring nation deploy equipment called Telex stations.
When a user wants to visit a blacklisted site, he or she would establish a secure connection to an HTTPS website, which could be any password-protected site that isn't blocked. This is a decoy connection. The Telex software marks the connection as a Telex request by inserting a secret-coded tag into the page headers. The tag utilizes a cryptographic technique called "public-key steganography."
"Steganography is hiding the fact that you're sending a message at all," Halderman said. "We're able to hide it in the cryptographic protocol so that you can't even tell that the message is there."
The user's request passes through routers at various ISPs, some of which would be Telex stations. These stations would hold a private key that lets them recognize tagged connections from Telex clients. The stations would divert the connections so that the user could get to any site on the Internet.
Under this system, large segments of the Internet would need to be involved through participating ISPs.
More @ bit.ly/pNB1xv
The system is called Telex, and it is the brainchild of computer science researchers at the University of Michigan and the University of Waterloo in Canada. They will present it Aug. 12 at the USENIX Security Symposium in San Francisco.
"This has the potential to shift the arms race regarding censorship to be in favor of free and open communication," said J. Alex Halderman, assistant professor of computer science and engineering at U-M and one of Telex's developers.
"The Internet has the ability to catalyze change by empowering people through information and communication services. Repressive governments have responded by aggressively filtering it. If we can find ways to keep those channels open, we can give more people the ability to take part in free speech and access to information."
Today's typical anticensorship schemes get users around site blocks by routing them through an outside server called a proxy. But the censor can monitor the content of traffic on the whole network, and eventually finds and blocks the proxy, too.
"It creates a kind of cat and mouse game," said Halderman, who was at the blackboard explaining this to his computer and network security class when it hit him that there might be a different approach -- a bigger way to think about the problem.
Here's how Telex would work:
Users install Telex software. Halderman envisions they could download it from an intermittently available website or borrow a copy from a friend.
Internet Service Providers (ISPs) outside the censoring nation deploy equipment called Telex stations.
When a user wants to visit a blacklisted site, he or she would establish a secure connection to an HTTPS website, which could be any password-protected site that isn't blocked. This is a decoy connection. The Telex software marks the connection as a Telex request by inserting a secret-coded tag into the page headers. The tag utilizes a cryptographic technique called "public-key steganography."
"Steganography is hiding the fact that you're sending a message at all," Halderman said. "We're able to hide it in the cryptographic protocol so that you can't even tell that the message is there."
The user's request passes through routers at various ISPs, some of which would be Telex stations. These stations would hold a private key that lets them recognize tagged connections from Telex clients. The stations would divert the connections so that the user could get to any site on the Internet.
Under this system, large segments of the Internet would need to be involved through participating ISPs.
More @ bit.ly/pNB1xv
Wednesday, August 17, 2011
Subscribe to:
Posts (Atom)